Will RCS support make iMessage interoperable?
You have to analyse every Apple announcement through the lens of how it plans to maintain its market power and attack regulation. So, will Apple’s promised Rich Communication Services (RCS) support make iMessage fully interoperable at least with Google’s Messages? What would the most grudging compliance with Chinese 5G regulations look like?
Continue reading


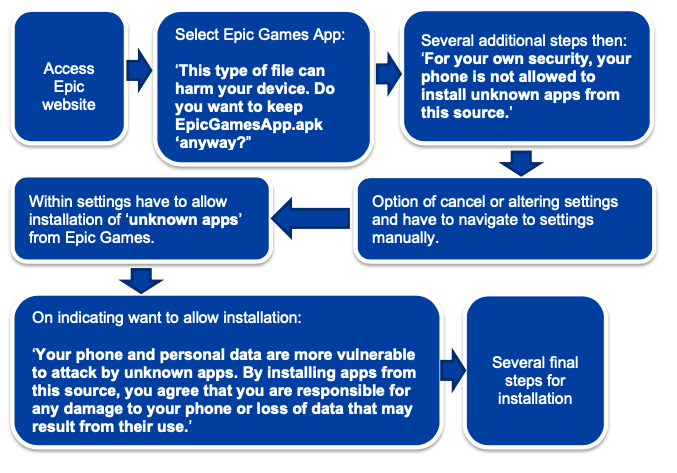




Recent Comments